Its a hoax perpetrated by people wanting to steal EBay logins with good feedback so they can post fraudulent auctions for cell phones and cameras that will never arrive after the buyers send their money in.
This has been going on for some time but the virulence of the recent messages suggests that the perps may have to be trying harder to get the response rate they need.
Another interesting development is the use of accounts with low feedback scores to post hoax auctions with bogus links that purport to be to send the user a message that are actually phishing links. A common ploy there is to advertise something at a ridiculous price to encourage another buyer to 'help them' by telling them they added a zero to the price by mistake.
Again why would they bother if it was still easy to steal accounts using spam?
When faced with a problem as bleak as phishing even the smallest signs of success is good news. It is clear that the barriers to entry in the phishing game are rising rapidly. That still leaves the big organized gangs of course but it will be easier to focuse on them with fewer small time bit players obscuring the view.
Monday, July 31, 2006
Alert eBay Unpaid Item Strike Received
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Ah but he's a profitable anti-Semite...
Arianna Huffington reports that Gibson has not become persona-non-grata in Hollywood yet.
Seems that he is still considered to be someone who might be costly to cross. Which is of course the point: there is not much morality in taking a stand on something only when its costless.
Its like the right to life protestor who has an abortion because having a baby would get in the way of her college plans but makes up for it by working extra hard on the picket lines to save another baby and make up for it.
Make that type of statement in Hollywood and your career as second grip, hairdresser or third extra would be over, Mel Gibson on the other hand is a different matter. The point is that second grips hairdressers and extras have little to no influence on the films Hollywood makes. Directors, producers and scriptwriters like Gibson do have influence and Gibson makes the most of his influence to insert subtle libels into his films.
The issue here is not just one momentary drunken outburst, it is the fact that what was said confirmed earlier evidence that Gibson is a bigot.
The reason he has received a pass so far is that for some reason religion gets a pass when it comes to bigotry. The reasoning seems to be that believing God to be a bigot somehow makes it OK.
The type of subtle libels Gibson inserts into his films have real effects. Wars have been started over less.
1 comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Sunday, July 30, 2006
The hate that dare not speak its name
Mel Gibson's anti-semitic tirade after being stopped for DUI has been confirmed.
This means that Mel Gibson almost certainly joins Michael Jackson and Tom Cruise as Hollywood A-List celebrities whose careers have been severely damaged if not ended by their private lives.
Unlike Jackson or Cruise however there are very good reasons to beleive that Gibson's private anti-semitism made its way into his films. It is difficult to see how he could get away with The Passion of Christ now.
Long before he was suspected of anti-semitism however Gibson's films were notable for their peculiar portrayal of British history. Soon after Gibson first came to notice in Mad Maxm Gibson starred in the 1981 movie Gallipoli which shows the Dardanelles campaign from Rupert Murdoch's perspective. This takes some liberties with the truth since Murdoch's objective is to vindicate the role of his father. Most notably the Australian Colonel J. M. Antill who commanded the attack is turned into a British 'Colonel Robinson' and a benevolent Australian general is invented who calls of the attack (this never happened).
In addition to taking liberties with the details of the campaign the movie is based on a much larger fictions that the original strategy behind the campaign was flawed and that the Allies were more careless with colonial lives than their own troops. The British gernerals were equally careless regardless. And that was why Winston Churchill argued for the Dardanells campaign in the first place, unlike the pointless battles taking place over a few yards of undifferentiated territory in France the Dardanells campaign had a clear strategic goal: to cut the Germans supply lines to the Arabian oil fields. The German capitulation finally came after this was finally achieved in 1918. It is now known that the 1915 campaign had a much better chance of success than was realized at the time, the Turkish forces were at one point in retreat until they were rallied by a then unknown commander Mustafa Kemal later known as Kemal Ataturk.
The distortions of Galipoli might be dismissed as mere historical license if not for the fact that Gibson's later films Braveheart and The Patriot both share the same approach.
The film Braveheart is based on the spurious claim that Edward I launched an invasion of Scotland with the intention of destroying the indigenous population of the country. While such things certainly happened in the 19th and 20th centuries the concept of a 'nation' let alone a 'state' in the modern form simply did not exist at the time. The idea of massacring peasants or rather serfs as they then were would make no more sense to the medieval mind than massacring cattle, sheep or any other chattel that had belonged to the other side.
Nor was there any need since what we now know as 'guerilla' tactics had not yet appeared, Robert the Bruce is generally credited with having invented them.
There is certainly no evidence for the claim made in the film that Edward I invoked the 'ancient law of 'jus primae nactis', there being no evidence whatsoever that such a law ever existed or was even referred to as having existed until the late middle ages.
The other dimension Braveheart deliberately conceals is the fact that the Highland tribal Lairds shown in the film were in fact largely descended from the same stock as the Norman aristocracy in the South. Guido de Baliol, the ancestor of the John de Balliol in the film was a Norman lord who fought with and for William the Conqueror. The first Scottish war of independence was really a dispute within the Norman aristocracy. Neither England nor Scotland existed in the form we now understand them as.
In the Patriot Gibson invents attrocities against civilians in a war notable for their absence. This is acknowledged in the script where the audience is told that the event may not appear in the history books.
Update: Gibson later referred to his comments as 'unspeakable', hence the title.
In Hollywood some bigotries are acceptable and others are not. He won two Oscars for Braveheart. Those are probably going to be his last. I don't claim that anti-British bigotry is as big a problem as anti-semitism, clearly it is not. Even so Gibson's personal contribution to the field of anti-semitism is likely to be somewhat minor while his anti-British libels have gained much wider currency. At root he is clearly a man who has a deep seated sense of grievance and hatred that he wishes to spread.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
'Access controlled by a password'
Emergent Chaos is debating Indiana's Breach Law, in particular the 'lost laptop' clause:
(2) Unauthorized acquisition of a portable electronic device on
which personal information is stored if access to the device is protected
by a password that has not been disclosed.
It probably makes sense to have an exception of this type in the first instance when the law is enacted. Otherwise we may well drown in privacy disclosure notices.
In the longer term the problem with such exceptions is that lost laptops are a major cause of data loss and there is at least anecdotal evidence to suggest that stolen laptops do trade for the information on them.
I suspect that at some point someone will point out that in practice a laptop disk is only password protected in a meaningful sense if and only if the data is actually encrypted. Otherwise it is a trivial matter to mount the disk on a different machine and read the data. Since file encryption is now available on Windows as part of the base build and Linux as several well supported packages there is no real excuse for not using it.
Ultimately there will be a requirement to apply content management to privacy sensistive data as a matter of course.
2
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Wednesday, July 26, 2006
Cyberwar reaches the blogosphere
There has been an ongoing Israeli/Palestinian cyberwar going on for quite a few years now. Originally started by a group of Israeli hackers bent on taking out Hamas and Hezbollah sites their opponents quickly retaliated in like measure. At this point the Israeli hackers have long ago run out of targets and are now high priced consultants selling their security services to the Israeli companies whose sites are attacked by the Palestinian hackers who are unlikely to run out of targets any time soon.
Instead of taking the sites offline with a DoS attack or putting up graphiti the Palestinian hackers used the attacks to distribute propaganda. This technique seems to have now reached the blogosphere as I try to link to Cool Web Tool and instead reach a page of what seems to be pan-Islamic propaganda.
It will be interesting to see what happens from here. It may signal that US targets are now being targeted or it might be just a means of getting the propaganda out there. Time to improve blog security.
Update: The site has been fixed. Looks like its machine generated pages to pull in search engines.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
I want my OpenID!
Getting tired of having to remember all those usernames and passwords for every Web site you use? OpenID is an attempt to solve this problem so you can use one account at any Web site that supports OpenID.
The folk at I want my OpenID! are running a bounty program for open source developers that OpenID enable their code.
Unlike previous 'single sign on' schemes such as Passport OpenID is open in every way. Anyone can set up an identity provider. Anyone can make use of the identity assertions issued.
Having a portable identity is the first step to having a portable reputation. It would be nice if there was a way to make use of your Slashdot karma at sites other than Slashdot.
It may be some time before there is enough confidence in the system to use it as a way to log into your bank account or for payment tranfers. But in the short term OpenID can do a lot to stop phishing getting worse by reducing the current proliferation of user accounts that people have to deal with. Most people use the same username and password in every place that they are allowed to.
Perhaps one day it will be possible to log into Slashdot using an OpenID, or even to leave a comment at this blog!
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Tuesday, July 25, 2006
Search terms
So I write a blog about Internet crime and 100% of all the searches leading to the blog are people trying to find out about junk telemarketers. My stats service only gives the details on my last 100 hits unless enough people click on the ads so I can pay for the upgrade.
34 51.52% 949-419-1007
11 16.67% 877-256-7894
5 7.58% (949) 419-1007
4 6.06% 877-256-7879
4 6.06% 949 419-1007
3 4.55% 708-539-2373
2 3.03% 949 419 1007
1 1.52% 877 256 7894
1 1.52% 949-419-1007 phone number
1 1.52% (949) 419-1007
Needless to say, it is difficult to see how 150 people a day would be trying to find out about these people if they actually asked for information through the Web as they claim. Moreover one might expect that Google would have an entry for the 'Assured Lenders' Web site.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
A taxonomy of spam
A lot of people seem to be getting confused when we explain that DKIM will act on some types of spam but not others. This naturally leads to the question 'what spam will it affect?' at which point we have no clearly defined taxonomy. During early anti-spam actigvity there were long flamewars over the definition of spam and so the topic of defining what spam is was quickly declared off limits. As a result we never established a taxonomy of types of spam, it remained a single undifferentiated problem despite the fact that we knew that there were different degrees of spam and that no single technology would eliminate all of them.
Spam: a communication regardless of medium that is originated indiscriminately and likely to be unwanted by the recipient.
This definition eliminates very little, about the only form of unwanted communication that is excluded is things like writs, bills and such. While they may not be wanted by the recipient few of us would consider them spam.
We then subdivide spam according to two orthogonal axes: by communication medium; email, phone, etc. and by category, the two principal categories being criminal spam and non-criminal spam. Within each heading we have a series of possibly overlapping subclassifications.
Within criminal spam we have social engineering attempts (phishing), malware attacks (viruses, trojans, etc.), advance fee fraud, consumer fraud, theft of service, impersonation of origin.
Within non-criminal spam we have unsolicited commercial messages, chain letters.
Once we have a taxonomy it is much clearer that DKIM is designed in first instance to address the theft of service and impersonation of origin categories directly and may thus have a significant effect on criminal spam in general. DKIM is unlikely to have a great effect on unsolicited commercial messages unless and until there is an accreditation/reputation system to back it.
The purpose of CANSPAM also becomes clearer. While most spam that violates CANSPAM was already criminal before the act passed the act is still usefull because it serves as a tripwire offense enabling law enforcement to determine that a crime has occurred much sooner than without the law. CANSPAM does not change the legality of the spammers behavior but makes it easier to prosecute acts where the criminality is beneath the surface
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Monday, July 24, 2006
Where bogus Watch list entries come from
So now we have quotas for suspicious activity that air Marshalls are expected to meet. No reports, no raise.
As a result the genuine information being gathered is being polluted by bogus entries put in by people who were making sure of their raise. In the end the good data will end up being thrown out because it is not possible to sort the good from the bad.
Graham Greene wrote about this type of activity in 'Our Man in Havana'. It is a good read by a former intelligence officer.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Friday, July 21, 2006
How not to write Device Drivers
The recent installation of a new KVM switch has caused me to think a lot about device drivers. I have concluded that the current approach to writing device drivers is completely wrong.
The mistake is the idea that we should be coding device drivers at all.
This was brought home to me while installing the KVM switch on my locked down machine with absolute minimal user privileges. This required seven (count them!) different device drivers, none of which were signed despite the fact that they were all written by Microsoft. First the KVM switch announced itself as a USB hub. Then a 'Human Interface Device' driver was loaded to serve the mouse followed by a mouse specific driver. This was then repeated twice for the keyboard, the first time for the normal keyboard keys and the second time for the extra keys to do things like control audio volume.
Plug and play was a good idea, signing drivers was a good idea. The idea that every new device should add new code into the kernel space is terrible.
There will always be a few oddball devices that absolutely must use custom code. But 95% of devices should be able to use a small number of tried and tested generic drivers.
Today every model of every printer has its own driver. There must be at least 500 printer drivers that ship with Windows but the vast majority are simply variations on Postscript, PCL and the ancient Epson dot matrix codes.
Adding a disk drive to a system is much easier. There are built in generic drivers for all the common disk drive interfaces (IDE, SCSI, SATA, etc.)
Early experience with flash memory on the other hand was rather more mixed. Early flash memory would often insist on announcing itself as being made by a specific manufacturer resulting in tedious requests to load device drivers that were all the more irritating because the chips themselves were mostly made by the same two manufacturers who supplied them to a much larger number of companies who just had to put their own brand on them even if doing this caused the user to have to install an entirely unnecessary custom device driver.
Generic device drivers are safer and more convenient to install. The downside is that the current generic drivers do not provide the same functionality as a fully custom driver. The generic print drivers do not support choice of paper size, print trays and so on but there is no reason they should not. A simple printer capabilities query protocol would allow the pronter to tell the operating system the feature set it supports and the options the user may select. In the rare case that a printer did require support for a non-standard page description language the code to support this should run in application space and not the kernel.
Deciding that the driver of choice should be the generic driver has other dividends. The user interaction step in the device installation process can be bypassed completely. The driver can be pre-loaded into the operating system and configure automatically.
This is going to be increasingly important as the computer user is taken out of the administration loop for more and more operations and particularly as Virtual Machine technology is deployed to provide a line of defense against rootkits. Logging in to the machine with administrator privileges, even accessing the base machine is going to become increasingly difficult. This is not going to be acceptable if new code has to be inserted into the kernel to support every keyboard, mouse and web cam on the market.
Best of all the security issues that result from loading buggy or outright malicious device drivers are largely avoided. If a device driver is buggy it is much more likely to be patched.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Identity theft can get worse
Just as you thought identity theft was bad but perhaps manageable Jonathan Rusch has
some examples of identity theft that should really worry you.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Thursday, July 20, 2006
Bogus phone call of the day - 866-325-2373
I just recieved a hang-up call from 866-325-2373. This is the second time they have called, they did not leave a voice mail and they hung up when I answered. Google
Search results in a series of hits on the Free Republic Web site.
One possibility is that they are using some sort of auto dialer and they simply drop calls placed if there is no-one to handle the call.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Wednesday, July 19, 2006
Moore's law - why does it work?
People speculate endlessly about how long Moore's law can continue. Why does nobody seem to ever ask why it works in the first place?
We take it for granted that computers are always getting faster. Moore's law predicts that the number of transistors on a single integrated circuit will double every 24 months.
Technology should improve over time. Each computer generation provides better tools for building the next. What is astonishing about the Moore's law is its regularity and predictability over a period of more than 30 years.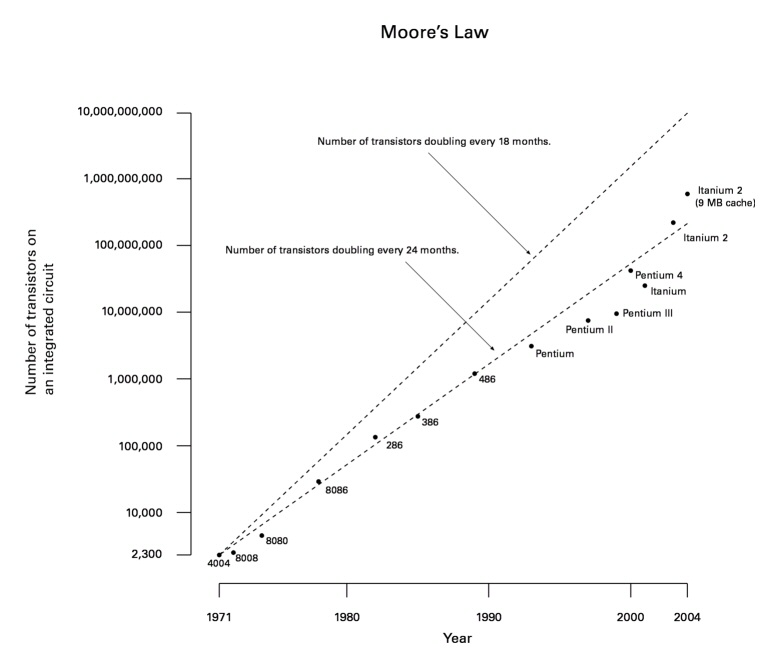
When a phenomena is as reliably predictable for so long there must be some sort of control mechanism at work regulating it. Why 24 months? Why not 36? or 12?
I suspect that the explanation for Moore's law is probably Moore's law itself. Production of ICs is a complex process requiring many steps. Each reduction in the minimum feature size requires advances in many different fields. Silicon crystals must be grown that have fewer defects. Lithography techniques must advance to the next level as must the techniques for cutting the mask. Deposition and polishing techniques must improve.
Improvement in only one area is no use unless the other areas make the necessary improvements and so whenever a particular area appears that its rate of progress may cause it to fall short of the demands of Moore's law considerable additional effort is concentrated on the problems to ensure that this does not happen. The dependence on progress in other areas means that the reward for progress that is too far in advance of Moore's law in a single isolated area is limited.
Ultimately Moore's law becomes the metronome that regulates the progression of the state of the art. Chip makers and the equipment manufacturers who supply them both aim to deliver technology that is just slightly ahead of the demands of Moore's law at the time. If either fails to deliver on time it will be quickly replaced by a competitor who does.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Tuesday, July 18, 2006
Mortgage cold caller Markus edges out Paul from the Prize Claim Center
It looks like I am not the only person getting the calls from the mortgage company. since my first post on the call from 949-419-1007 it has surpassed Paul from the Prize Claim Center and is now responsible for over 50% of the traffic comming to this blog through search terms.
Before assuming that this means that Markus is being bussier than Paul it is quite likely a result of the different placements in the search engines. Several sites report on Paul's activities, this blog is #4 in the Google rankings for "708-539-2373". It appears that I am the only person blogging on Markus so far.
Just to be clear I have no reason to beleive that these particular scams are anything other than what they appear to be. The reason that I beleive that condign measures should be applied with urgency now is what I expect to follow if they are left unchecked.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Saturday, July 15, 2006
Junk phone calls or VOIP phishing?
The Do-Not-Call list has put a stop to most Junk marketting calls but there are still calls comming in on my mobile number which was off limits before Do-Not-Call came in.
Todays call came from a company that sounded like 'Assured Lenders', a person calling himself Markus. The call back number was 1 800-606-1470, the caller ID was 949-419-1007. Calling back either number resulted in another recording that puts you on hold.
When I called the number back the phone was answered by a woman. She tried to claim that they were not cold calling but the speed with which the response was made made it obvious that she was hearing many complaints.
As with the email spammers these people have picked up ways to try to disguise the fact that they are cold calling, claiming to be responding to an internet enquiry. This claim is not very believable. How many mortgage companies respond to customer enquiries with a recorded voice message asking them to call back at another number?
How long before the VOIP phishing people use the same strategy? The FCC needs to make putting the cold callers of all types out of business a priority. Otherwise the outright criminal will quickly replace the nuisances.
3
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Friday, July 14, 2006
Iran
I don't intend to make a habit of blogging on political issues in this particular blog but I see a major omission in the current discussion of the situation in Israel/Syria/Lebanon.
The question we should be asking is whether the parties are behaving rationally or irrationally. If the parties are behaving rationally there is a very good chance of containing and de-escalating the current crisis. If on the other hand one or more of the parties are irrational we may be headed for a third major conflict in the region and civilian casualties on each side are likely to number in the thousands, tens of thousands or more.
Al Qaeda is clearly an irrational actor. The attack on the US vastly underestimated their strength, resolve and likely response. It is one thing to defeat the USSR in a conflict where even the Soviet union could not remember what their original strategic goal was, quite a different matter to defeat a superpower after an unprovoked attack on a civilian target.
Fortunately the causal nexus in the latest escalation is not Al Qaeda, it is Hezbollah which in turn is generally regarded as a front for Iran. There are two possibilities therefore: Hezbollah may be acting on behalf of Iran or it may be freelancing. In the short term we are unlikely to find out which of these is the case. If Hezbollah is freelancing it may be beyond Iran's capability to rein them in before the next escalation of the crisis tips the region into all out war.
If Hezbollah is not freelancing it is under control of Iran. Over the past five years Iran has finessed a strategically weak situation and established itself as the second regional superpower. Iran's has built this situation through tactics that are aggressive but not irrational. In particular Iran has encouraged its perceived enemies to attack each other rather than Iran.
In the wake of 9/11 the 'Axis of Evil' speech made by President Bush amounted to a statement of intent to declare war on North Korea, Iran and Iraq. At the time Iran had friendly relations with North Korea and hostile relations with Iraq. In this situation a rational course of action for Iran was to encourage the US to make war with Iraq first and collaborate with North Korea to build a nuclear deterrent.
Given Iran's previous rational behavior we should be reluctant to jump to the assumption that their current (assumed) behavior is irrational. On the contrary it is entirely rational for Iran to assume that the Bush administration will continue efforts to build a case for invasion of Iran as the 2006 mid-term elections approach and entirely rational to seek to pre-empt a pre-emptive strike against their ongoing nuclear program through the current escalation of tension in the region.
At this point the political imperative of the US establishment is to prevent an escalation to all out war in the region. If as I believe Iran is behind the current escalation they are providing a dramatic demonstration of the cost of an attack against them. The number of members of the US establishment who beleive that Iran could be attacked with impunity must have dropped significantly in the past few days.
It is now highly unlikely that the opponents of a new war with Iran are going to be intimidated as easily as the Congress was when it authorized the invasion of Iraq. It is clear that Iran has both the means and the will to retaliate.
If the Iran hypothesis is correct the key to bringing the current situation to resolution is for the US to convince Iran that any possibility of an attack on Iran has been foreclosed. Only once this has happened will Iran order its proxies to de-escalate the crisis.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Wednesday, July 12, 2006
Google blunders
So I connect to Google here at the Montreal IETF. Only I don't get Google, I get Google Canada.
This probably seemed like a good idea to the Google people, customize Google for every locale, use IP address lookup to determine the locale.
The net result is that when I type www.google.com I get redirected to Google Canada rather than get my own personalized home page with the news, email etc resources I have selected. And when I click on 'Presonalized Home' I get directed to the Canadian silo not my own personalized home page.
1 comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Tuesday, July 11, 2006
Why Does WiFi have Ad Hoc mode?
I am at the 66th IETF and so it is time to ask 'why does WiFi have ad hoc mode?'
As near as I can make out the only use for ad hoc mode in WiFi is to provide a ready means of performing a denial of service attack. If you have a lot of laptops in a small space together running off a common access point (or two) they usually get along pretty well. If you have someone running in ad hoc mode they are chewing up as much bandwidth as the access point.
So the usual pattern at these events is the room fills up, the network gets a little slow. At some point some dweeb decides for whatever reason that the speed of the network is intollerably slow. They start fiddling with their network settings trying to make the thing faster. At some point they ask 'what does ad hoc mode do'. They try it out and in the process cause some folk to loose their connection to the access point.
So then they start to fiddle and they see the ad hoc network being advertised 'what is this' they ask and they try to connect. So now we have two ad hoc networks, then three and four. And each time more of the bandwidth gets gobbled up and more people start to fiddle and the situation gets worse.
Eventually the point is reached when the meeting chair has to ask people to shut down their computers if they are using ad hoc mode before the sheer volume of microwave radiation in the concentrated space starts to slowly cook people from the inside out.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Sunday, July 09, 2006
Clueless dotcom business models
Imagine that you are an investor in a startup planning to spend $4bn to develop an infrastructure. The startup is entering the market over a decade later than the incumbent who gives their product away for free. In this situation the security of your encryption codes should probably not be your first concern.
If there was no GPS system available for civilian use Gallileo would be a fantastic idea: establish a system of global positioning satelites and charge device manufacturers a fee for making use of it.
With GPS in place and the signal being made available for free the only value in Gallileo is either insurance against the US withdrawing service for the system or to provide positioning data that is somehow 'better'.
It may be logical for the European Union to invest $4 billion to ensure that they are not dependent on the US for such a critical infrastructure. It is utterly illogical for me as a private individual to do the same to protect the value of by in car GPS unit.
The value of Gallileo lies in the ability to claim a seat at the negotiating table if there is a realistic possibility of turning the signal off. There is a small probability that the result of the discussion would be a situation where more information was available on Gallileo than GPS but it is not very significant. If this does happen it is most likely to be a temporary annoyance I can live with. There is a much higher probability of either my machine breaking or the Gallileo project folding like Iridium and Telestra.
The investors in Gallileo must know this as well. What is it that we do not know? The only way Gallileo makes sense is if makers of GPS units are required to license the Gallileo technology to sell them in Europe.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Saturday, July 08, 2006
XenSource
I have been looking at virtualization as a mechanism for defeating rootkit technology and other types of Trojan for some time.
Microsoft has been working on this type of scheme for some time. It is likely to be the only way to manage the transition from entirely unrestricted consumer O/S to a system where Winnie the Pooh Treehous game cannot insist on having full root privileges to run. One of the open questions has been how to get this technology adopted into the Linux mainstream. The OSS world is great at developing niche technologies to support ultra security for a few. It is much less good than it thinks in deploying state of the art security to the masses.
That is why XenSource is so interesting. Xen is not a full virtual machine implementation, it is a para-virtual machine. Instead of pre-empting instructions at the CPU level this takes place at a different layer in the stack. The architecture ends up looking remarkably like Butler Lampson's security monitors.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Thursday, July 06, 2006
Interview in Investors Business Daily
I did an interview with IDB last week, it came out this week.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Wednesday, July 05, 2006
NYT on phishing crook
The NYT article on the activities of an 'identity theif' (i.e. a pishing scammer) raises some interesting points:
First Sharma was caught after he bought an ID card printer on a stolen credit card and had it delivered to himself. This strikes me as a pretty rookie mistake. If there is a single transaction that would set off alarm bells it would be the purchase of equipment used to make credit cards.
Most cases if a merchant gets a chargeback on a credit card they just eat it. Cops are not that interested in investigating individual credit card frauds. When the goods bought are clearly tools for financial fraud then heaven and earth will be moved if necessary.
Second, his screen name, sniper5984 was his birthday! Of all the rookie mistakes immaginable that is pretty crass.
Third, probably the most important. It may be true that the cops only catch the stupid criminals but they only need to be stupid once (buying the printer) and smart criminals who associate with stupid criminals put themselves at risk.
That is the reason why organized crime is rare. It is very hard to establish the necessary discipline and critical mass. Organized crime can make real money but the centrifugal forces are always pulling the organization apart. It takes a very strong centripetal force to keep everything pulled together.
It only took one weak link in the chain to bring down Shaddowcrew and Carder planet. Shama's prison sentence of 2 to 4 years is remarkably short for someone who stole $150,000 on their third conviction. He clearly provided a lot of cooperation.
Looking through the backups of carder portal, sniper5984 had a bad reputation even amongst the carders. He was notorious as a 'ripper' (someone who takes money but does not deliver the goods). On one occasion he put out a message asking for 'donations' to a legal fund for a fellow carder 'greywolf' who turned out not to even be in jail (public archive)
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Tuesday, July 04, 2006
Reliable WiFi boxes, do they exist?
The WiFi is on the fritz again. I just had to switch in the backup box as our latest router begins to show the now familiar symptoms of the WiFi pox. It works well for a while until the WiFi part stops working without notice. After a reboot the box is fine for a while but the time between freezes steadily declines until it needs a reboot every hour.
Lucent, Linksys, Netgear, I have tried all the brands. My older netgear box still works but it is only 802.11b and the firmware does not support VPN passthrough (says it does but it does not work with our checkpoint VPN).
It is quite possible that part of the problem is caused by overheating. The older Netgear device has a nice metal case with plenty of ventilation holes. The new ones are pieces of plastic crap. Nobody seems to make a wireless router that has a built in power supply, they all have those obnoxious mains adapter plug things.
When the Linksys started to die the wireless service just shut down at random intervals. The Netgear has developed a similar but somewhat less critical problem, the DNS proxy shuts down and won't restart. This would not be a problem if there was a way of configuring the built in DHCP server so that it didn't tell machines connecting to it to use it as a DNS proxy. The only options provided are to turn DHCP on or off.
So now I have to turn on my VPN to surf the Internet and K's machine has the Comcast DNS server addresses hard coded. We can both surf the net fine at home but her machine has to be reconfigured to work outside the hose. The geniuses who wrote the Windows WiFi support code did not anticipate the need to store the TCP/IP settings as part of the connection profile.
The answer might be to get two of the new MIMO/pre-N routers which are meant to provide greater coverage in addition to greater bandwidth. I need two since the machines in my office run off an wifi to ethernet bridge. In principle it should be easy to configure any WiFi router to work this way. In practice only a few do it and those that do often don't say. My linksys travel router works that way but I only found out after I had bought it.
Online reviews are pretty useless as they are all of the 'open box, use it for a week, return' variety. The reviews are not long enough to demonstrate the reliability of the hardware.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Monday, July 03, 2006
The dangers of explanation
Ted Stevens (R-Alaska) got into trouble describing the Internet recently. Its a good example of why explaining technical issues to lay people is so hard.
The explanation he gives is not completely crazy and the points he is trying to make are somewhat valid. The problem is that he clearly does not understand the technology he is trying to explain.
Even people who do not understand electronics should know that mentioning 'tubes' is an unfortunate choice of language. If I hear the word tube I think of 1930s era valve radios. Vint Cerf or Tim Berners-Lee can get away with that type of analogy, nobody has any doubt about their technical knowledge. The starting assumption for a politician is that their understanding of the technical issues is superficial at best.
Net neutrality is not a technical issue, it is a political and economic issue. If there was a free market in telecommunications services the problem of net neutrality would be solved through the normal processes of competition. The problem with the Internet is that the free market ends roughly a three miles from the consumer's house. The 'last mile' has its name because it is the last mile to get built. We already have a fibre optic high speed Internet capable of providing 100 mb/sec to every house in the country. The problem is that today's last mile is provided by legacy cable and telco hookups. In most communities both are effective local monopolies.
Here in Medford I have a choice of getting my Internet from Verizon or from Comcast. As a result the effective price is $60 either way. To get that $19.99 Verizon DSL deal I have to have a Verizon phone line first. Same deal with the cable hookup, broadband is only cheap if it is bundled with another service.
Stevens makes a more powerful case than he intended. His clumsy analogy illustrates the best argument for not making regulations to require Net Neutrality at this point in time: the regulators do not understand the issues themselves yet.
The obvious rebuttal to this argument is that regulators should understand the issues they are trying to address. If Stevens does not understand the modern world it is time for someone else to carry out the task of legislating for it.
In the long term the outcome is more or less certain. Constituents have votes, corporations do not. Just as the telcos and cable companies ended up being regulated the ISPs will end up regulated if they outrage public decency.
In the short term Net Neutrality will continue to be a messy battle. It is unlikely that the campaign for Net Neutrality will gain fire outside the blogosphere until actual examples of monopoly abuse become more frequent.
The key to winning the battle is to develop technologies that open up the local loop monopoly. WiMax may be the answer. Fix a WiMax transmitter to every tenth utility pole and you have ubiquitous wireless networking.
Another approach would be to develop low cost methods of stringing optical fibre to the house. The raw materials required to make copper cable are vastly more expensive than the raw materials used to make fibre. Copper Coax cable currently costs $100 for 1000' vs $380 for fibre. Fibre optic is the material of choice in the developing world because its scrap value is zero.
Perhaps some cobination of these technologies is the answer.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Sunday, July 02, 2006
The US Coastguard says: F*** You
A member of the US coastguard responds to the evil genius post.
FUCK YOU ASS GROW UP
Actually the message was in 32pt Ariel but that is the text of the message. The point is that the message came from a uscg.mil address and it appears to be genuine.
This is an example of a problem a customer once described to be as 'emails too stupid to write'. Email is a powerful medium, an idea can be communicated across the world in less than a second. The problem is that many people put no more than a second's thought into the emails that they write.
The above memo being a case in point. If the person who sent it had realized that what he just sent is an official government communication from the Department of Homeland Security he probably would have thought twice before sending a message which sent to the wrong person could well be a career ending move.
Some people treat email like instant messaging but the recipients don't necessarily share the casual approach of the sender. The end result is that the company or in this case the service looks ill-disciplined and unprofessional.
Various approaches to fixing this have been considered, the latest fashion is for what amounts to an outbound spam filtering service to trap mail with expletives or other evidence of unprofessional conduct. They work about as well as you would expect them to, they reduce the nuisance value but don't stop the occasional atrocity slipping through the net.
I am a skeptic when it comes to user education, people are remarkably hard to educate. In this case though the goal has to be to change people's behavior. If people are writing emails with an Internet chat room mentality that attitude is going to be reflected in the rest of their work as well.
This is where I think Secure Internet Letterhead might help, or at least we should look to see if we can measure an effect. People might be less inclined to write unprofessional emails if they thought they were writing on company letterhead. They might even spend less time doing personal email on company time. Perhaps its wishful thinking but it is certainly worth checking.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Saturday, July 01, 2006
Evil genius seeks henchmen
Ever wonder how evil Geniuses like Dr No or Ernst Stavro Blofeld hired all those henchmen willing to be shot in the course of their plans for world domination? Wonder no longer, Craigslist!
Evil genius seeks henchmen
--------------------------------------------------------------------------------
Reply to: job-177591484@craigslist.org
Date: 2006-07-01, 10:37PM EDT
Must be expendable, physically fit, follow orders without question and wear uniform (provided). Previous experience with rockets, telecommunications and/or excavating the inside of volcanoes highly desirable.
Job location is various
Compensation: Monthly stipend (negotiable), room, board, ammunition, generous death benefits
yes -- OK for recruiters to contact this job poster.
no -- Please, no phone calls about this job!
no -- Please do not contact job poster about other services, products or commercial interests.
yes -- Reposting this message elsewhere is OK.
OK, I admit that I posted this myself. The point is that real criminals are recruiting people through the Internet to be mules for package reshipping and carding schemes. My post is obviously a spoof, their scams are much easier to fall for.
As with drugs trafficers, mules are expendable. The only difference is that an Internet money mover or package reshipper is certain to be caught. You could almost call it their job description. The carding ring does not want the goods they buy on Amazon with stolen credit card numbers shipped to their own address, too easy to be caught. So they have them sent to a package reshipper who forwards them by freight courier to the type of address Amazon would never ship goods to, like the West Africa or Eastern Europe, often the address is a loading dock of a warehouse.
When the mule gets caught the face a real risk of going to jail. Often the carding rings use the details they collected when they recruited the mule to perform an identity theft, that is taking out large loans in their name. In the case of money movers the transfers of stolen money into their account are fraudulent and are reversed. The transfers of money out of their account were properly authorized though and the banks will demand repayment.
Being an Internet mule is the job from hell: you end up with a tripple whammy of wrecked credit, a huge debt and likely jail time.
Update: We have our first applicant!
Update: Number of applicants is up to 3 in first hour!
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
6th Workshop on Privacy Enhancing Technologies
Adam and EKR have already blogged the paper on evading the great firewall of china, but there is plenty of interesting stuff in the rest of the agenda at the 6th Workshop on Privacy Enhancing Technologies
The firewall paper is likely to create the most interest because it describes the design of the Great Firewall of China and gives some insight into the thinking behind it. I have always thought that the GFC is more a question of face than a real attempt to prevent dangerous Western thoughts in. After all they already have Karl Marx and they don't get more dangerous than that. Besides which there are a billion people inside the firewall and they are the ones who know the information that is really damaging to the regime. They know about the corrupt local bureaucrats, the disasters, the repression. The only way anyone outside the country knows what is going on is that people inside tell them, and that includes the dissidents as well.
EKR discusses how to subvert the GFC by suppressing/ignoring RST signals. These are meant to tell the ends of a TCP/IP conection that the connection is over and there is no need to send additional data. In practice they are kinda redundant since the application protocols are designed so they don't rely on them.
A better way to circumvent the GFC would be to turn on encryption, or at least obfustication. The GFC uses IDS technology to detect sites that contain 'objectionable' strings such as FA-L!U-N+G. As my example shows it does not take a lot of effort to bypass systems of that sort. There are plenty of sites that obfuscate email addresses, why not have an IIS/Apache plug in that filters a site so that keywords known to trigger the GFC get encoded?
Reading between the lines is an old tradition in repressive regimes.
0
comments
![]()
![]() Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
Linkworks:
FARK
del.icio.us
StumbleUpon
reddit
